
Upgrading WiFi is straight forward, what needed are the usual ISP PPPoE username and password.
Out of the box, the ASUS BE3600 RT-BE58U contains factory generated password.



Upgrading WiFi is straight forward, what needed are the usual ISP PPPoE username and password.
Out of the box, the ASUS BE3600 RT-BE58U contains factory generated password.

For the TLDR Get start . Ventoy
Select and install your preferred version, either windows or linux
Run the program after unzip
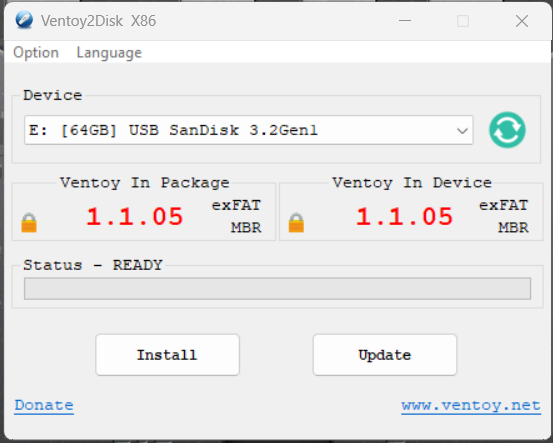
Click on Install button to install Ventoy into your USB drive.
Once it is done, open the Computer Management to verify Ventoy installation.
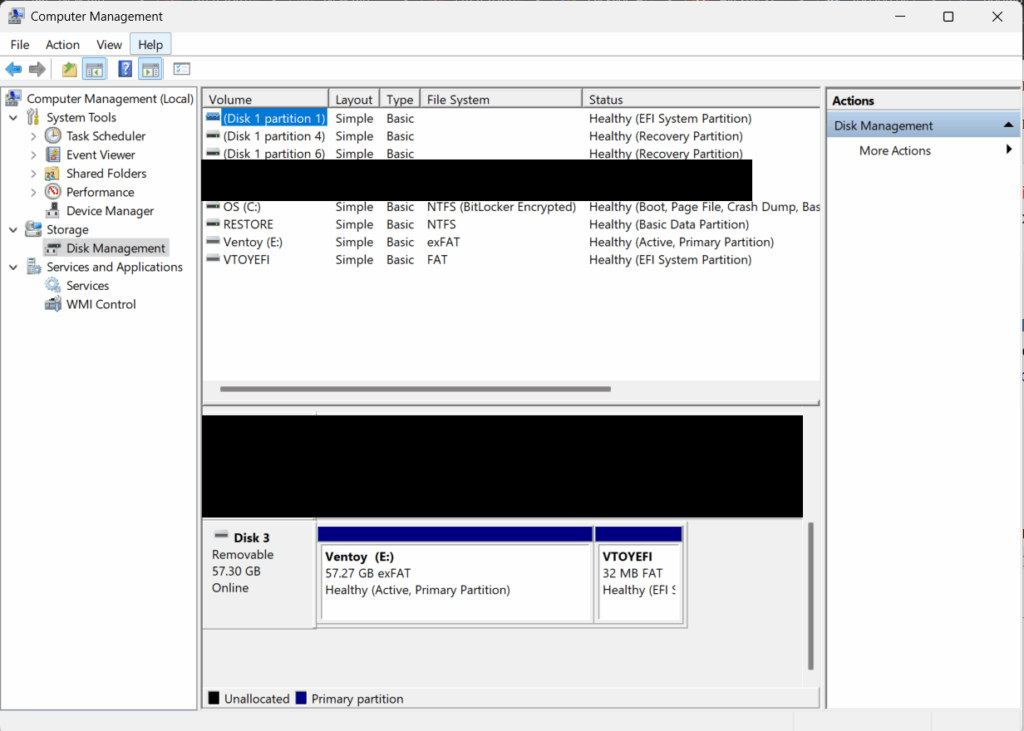
Upon install a partition VTOYEFI will be a 32MB partition in your USB drive.
Next place all your intended ISO into the counterpart partition.
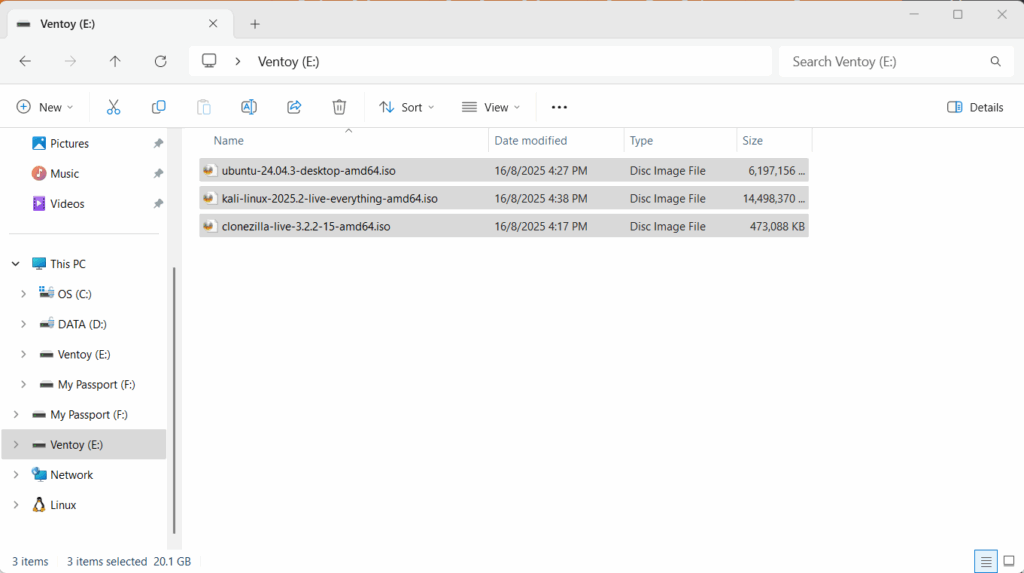
You can now boot a computer using Ventoy.
Based on Wazuh official documentation Wazuh Docker deployment – Deployment on Docker · Wazuh documentation
TLDR; just need to have docker engine installed on your favorite OS.
The next thing to do is to ensure your OS has a git client and run the following to clone Wazuh into your machine
git clone https://github.com/wazuh/wazuh-docker.git -b v4.12.0Next, generate the certificates that are needed by Wazuh to work. Make sure to decide to run on a single node or multinode indexer Wazuh. Go to the appropriate directory from the cloned Wazuh git repo. Then run
sudo docker-compose -f generate-indexer-certs.yml run --rm generator
If you are using the newer version aka Version 2 docker compose run the following instead
sudo docker compose -f generate-indexer-certs.yml run --rm generator
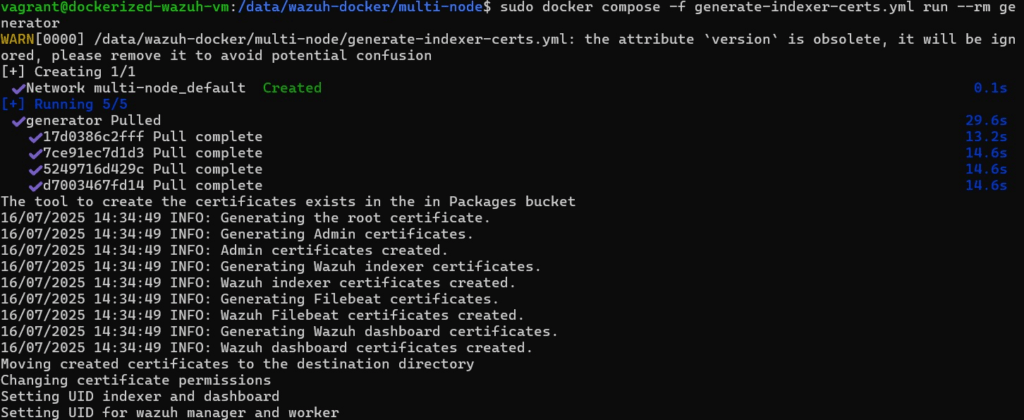
Once the certificate is installed, go to the correct directory then run the following:
sudo docker-compose up -d
Again, should version 2 of docker compose is used run the following instead
sudo docker compose up -d
If everything is good you will be able to browse to your Wazuh dashboard in a minute or 2.

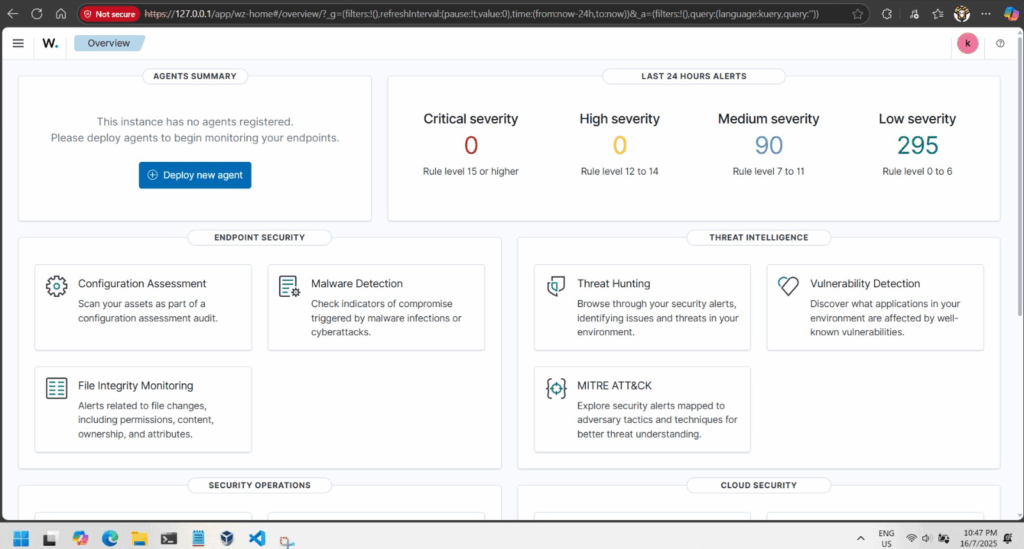
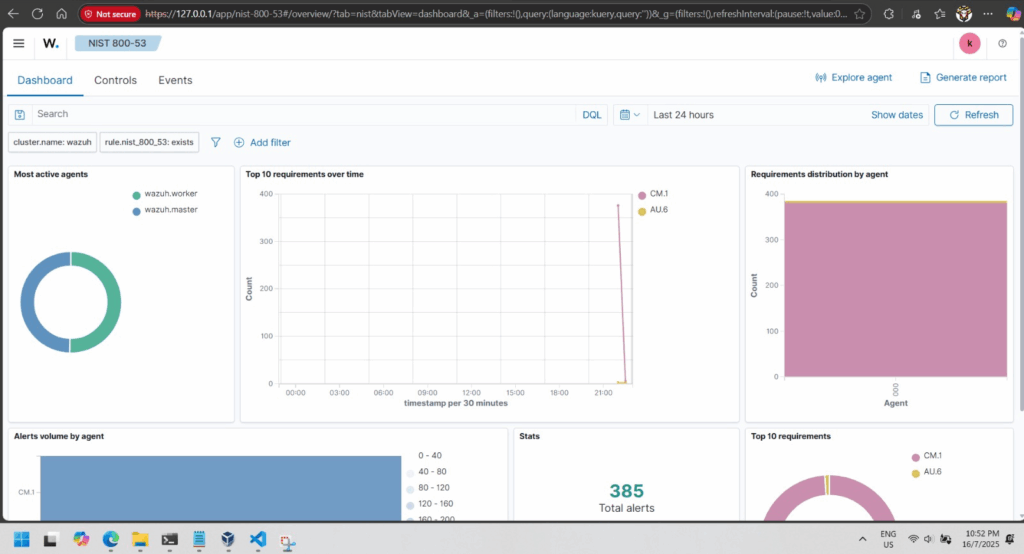
Wazuh SIEM (Security Information and Event Management) platform can help protect systems.
Wazuh SIEM Solution
Wazuh is a free, open-source tool that monitors systems, detects attacks, and logs security events.
It consists of:
Simulated Attacks & Findings
Security Recommendations
Conclusion
Wazuh helps organizations detect, analyze, and respond to cyber threats before they cause harm. By implementing strong security measures, users can protect their systems from the dangers of the “Wild Web.”
Final Thought: Cybersecurity is essential—tools like Wazuh make it easier to stay safe online!
Based on the previous post https://chow.karmeng.my/2025/03/28/programming-esp32-wrover-with-dht22-am2302-humidity-and-temperature-sensor/ , the breadboard that I had purchased has very unreliable connectivity. Resulting in signals from sensor not able to reach the ESP32 microcontroller board.
Upon hours of browsing, discovered expansion board module that is compatible with ESP32 and based on the price it does not break my pocket.

At the time of this post the price point offered is very affordable. I had order 2 pieces of the hardware.
Continue reading
Long story short, to make it work on ChatGPT, user need to ask the correct question after uploaded a photo.
To put into context, I am using ChatGPT free account that will require sign in, but I do not pay for it.
Continue readingReferring to the original material at ESP32 with DHT11/DHT22 Temperature and Humidity Sensor using Arduino IDE | Random Nerd Tutorials
The reference is straight forward; however, it is not for the esp32-wrover.
Based on the from the reference, using educated guess without reading the specification, it is a hindsight that the original wiring will not work.
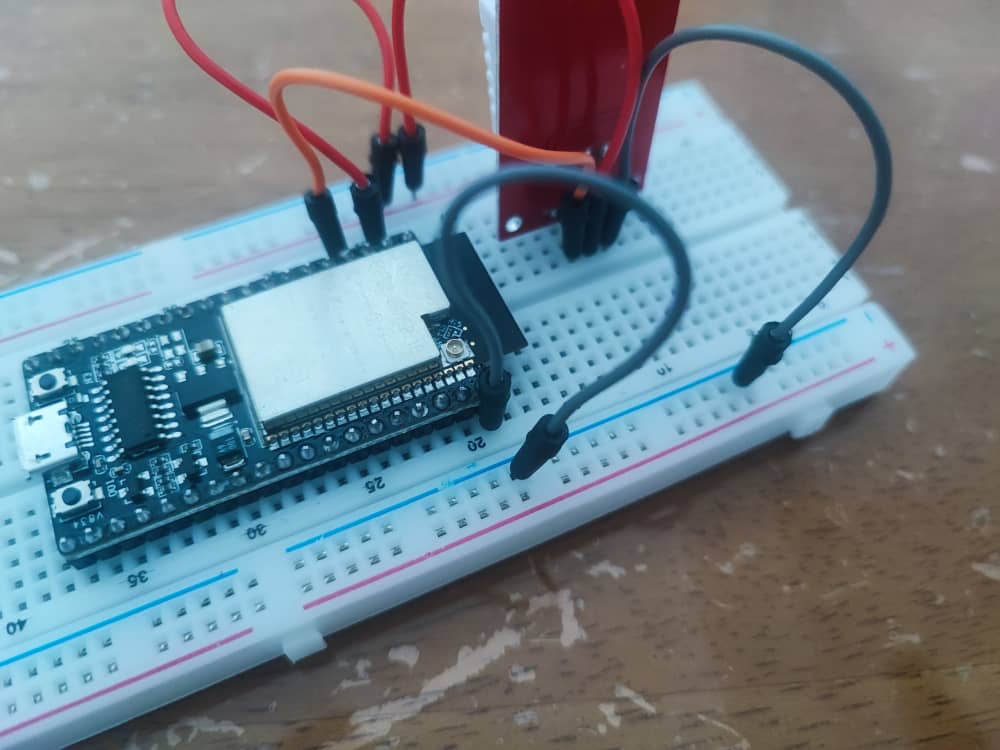
It didn’t work, was getting the error “Failed to read from DHT sensor!” from the sample code.
DHTPIN were used is 4, which I had wrongly assumed it to be the physical pin number. Little did I know that, the reference is referring to GPIO4 instead of the physical pin number.
Based on the reference, ESP32-wrover spec sheet page 9, the physical pin 4 is the SENSOR_VP.
Continue readingThis post is based mostly on Installing ESP32 Board in Arduino IDE 2 (Windows, Mac OS X, Linux) | Random Nerd Tutorials it is a good resource to get started on verify the ESP32-WROVER is working.
The hardest part is to determine what are the connector chip and installing libraries into Arduino IDE. Refer to the shared link in the beginning of this post.
Code from DeepSeek for a complicated hello world, assuming to make the LED blinks in morse code:
#include <Arduino.h>
#define LED_PIN 2 // Built-in LED on GPIO 2
// Morse code representations for A-Z
const char* morseCodes[] = {
".-", // A
"-...", // B
"-.-.", // C
"-..", // D
".", // E
"..-.", // F
"--.", // G
"....", // H
"..", // I
".---", // J
"-.-", // K
".-..", // L
"--", // M
"-.", // N
"---", // O
".--.", // P
"--.-", // Q
".-.", // R
"...", // S
"-", // T
"..-", // U
"...-", // V
".--", // W
"-..-", // X
"-.--", // Y
"--.." // Z
};
void setup() {
pinMode(LED_PIN, OUTPUT); // Set the LED pin as an output
Serial.begin(115200);
}
void loop() {
String message = "SOS"; // Message to transmit in Morse code
message.toUpperCase(); // Convert message to uppercase
// Transmit the message in Morse code
for (int i = 0; i < message.length(); i++) {
char currentChar = message[i];
if (currentChar >= 'A' && currentChar <= 'Z') {
transmitMorse(morseCodes[currentChar - 'A']); // Transmit Morse code for the character
} else if (currentChar == ' ') {
delay(1400); // Gap between words (7 units)
}
delay(600); // Gap between letters (3 units)
}
delay(2000); // Wait before repeating the message
}
// Function to transmit a Morse code pattern
void transmitMorse(const char* morseCode) {
for (int i = 0; i < strlen(morseCode); i++) {
if (morseCode[i] == '.') {
blinkDot(); // Transmit a dot
} else if (morseCode[i] == '-') {
blinkDash(); // Transmit a dash
}
delay(200); // Gap between dots/dashes (1 unit)
}
}
// Function to blink a dot (short flash)
void blinkDot() {
digitalWrite(LED_PIN, HIGH); // Turn the LED on
delay(200); // Dot duration (1 unit)
digitalWrite(LED_PIN, LOW); // Turn the LED off
}
// Function to blink a dash (long flash)
void blinkDash() {
digitalWrite(LED_PIN, HIGH); // Turn the LED on
delay(600); // Dash duration (3 units)
digitalWrite(LED_PIN, LOW); // Turn the LED off
}Code to connect to WiFi:
#include <WiFi.h>
// Replace with your network credentials
const char* ssid = "myhome4iot";
const char* password = "i have the longest wifi password ever";
void setup() {
Serial.begin(115200);
// Connect to Wi-Fi
WiFi.begin(ssid, password);
Serial.println("Connecting to Wi-Fi...");
// Wait for connection
while (WiFi.status() != WL_CONNECTED) {
delay(1000);
Serial.print(".");
}
// Connection successful
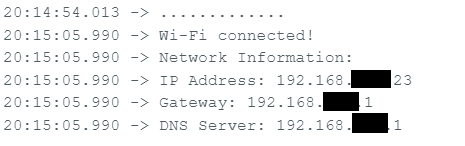
Serial.println("\nWi-Fi connected!");
// Get and print network information
IPAddress ip = WiFi.localIP();
IPAddress gateway = WiFi.gatewayIP();
IPAddress dns = WiFi.dnsIP();
Serial.println("Network Information:");
Serial.print("IP Address: ");
Serial.println(ip);
Serial.print("Gateway: ");
Serial.println(gateway);
Serial.print("DNS Server: ");
Serial.println(dns);
}
void loop() {
// Nothing to do here
}
Code to scan WiFi:
#include <WiFi.h>
void setup() {
Serial.begin(115200);
// Set ESP32 to station mode
WiFi.mode(WIFI_STA);
WiFi.disconnect(); // Disconnect from any previous connection
delay(100);
Serial.println("Starting Wi-Fi scan...");
}
void loop() {
// Scan for nearby Wi-Fi networks
int numNetworks = WiFi.scanNetworks();
if (numNetworks == 0) {
Serial.println("No networks found.");
} else {
Serial.print(numNetworks);
Serial.println(" networks found:");
for (int i = 0; i < numNetworks; i++) {
// Print SSID and RSSI for each network
Serial.print(i + 1);
Serial.print(": ");
Serial.print(WiFi.SSID(i)); // SSID
Serial.print(" (");
Serial.print(WiFi.RSSI(i)); // Signal strength (RSSI)
Serial.print(" dBm)");
Serial.print(" [");
Serial.print(getEncryptionType(WiFi.encryptionType(i))); // Encryption type
Serial.println("]");
}
}
Serial.println("-----------------------------");
delay(10000); // Wait 10 seconds before scanning again
}
// Function to convert encryption type to a human-readable string
String getEncryptionType(wifi_auth_mode_t encryptionType) {
switch (encryptionType) {
case WIFI_AUTH_OPEN:
return "Open";
case WIFI_AUTH_WEP:
return "WEP";
case WIFI_AUTH_WPA_PSK:
return "WPA";
case WIFI_AUTH_WPA2_PSK:
return "WPA2";
case WIFI_AUTH_WPA_WPA2_PSK:
return "WPA/WPA2";
case WIFI_AUTH_WPA2_ENTERPRISE:
return "WPA2 Enterprise";
case WIFI_AUTH_WPA3_PSK:
return "WPA3";
case WIFI_AUTH_WPA2_WPA3_PSK:
return "WPA2/WPA3";
default:
return "Unknown";
}
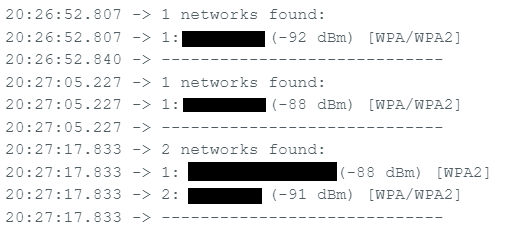
}Unfortunately, due to the ESP32-WROVER hardware limitation, any modern 5GHz WiFi will not be able to be scanned or detected. On top of that, the stock ESP32-WROVER-IE needs to have a actual wifi cable to extend its range.
Type in nvcc –version from your Jetson Nano terminal is the sure way.
If the nvcc is missing, it could mean that the jetson-toolkit were not installed, or the binaries was not added to your session.

The commands to reassociate.
Continue readingAfter forcing the Jetson OS (based on the ubuntu 18.04) to have Python 3.8 running. After having the JetPack 4.6.3 installed in the Jetson Nano Jetson OS.
When attempting to install TensorFlow 2+ manually in the Jetson Nano based on Official TensorFlow for Jetson Nano! – Jetson & Embedded Systems / Jetson Nano – NVIDIA Developer Forums

Or running the pip3 install command:
sudo pip3 install --pre --extra-index-url https://developer.download.nvidia.com/compute/redist/jp/v46 tensorflowAfter a long time installing all the dependency for TensorFlow. A dreaded error message will occur.
ERROR: Failed to build installable wheels for some pyproject.toml based projects (h5py)

To understand the error, scroll up to read what are the error.
Continue reading